Let's face it...password management is not fun. We all know it is bad practice to use the same password across multiple sites, and the most secure password is one that you can't remember. We should all probably be making sure we change passwords at a regular basis, yet how many of us still have a tendency to use the same password, or a slight variance of the same password for most of our logins? I know that I have been guilty of this. Fortunately, with tools like 1Password, LastPass, & KeePass I have been getting better at my personal password management techniques.
What about our company password management techniques? How many of us IT Pros have knowledge of one or two passwords that if placed in the wrong hands could open the 'Keys to the Kingdom'. Perhaps it is the root password for our ESXi hosts, or the SQL service account password with dbowner rights. It might be the elevated Domain Admin account password. I am sure if we think about it, there is at least one password we all know in IT that carries with it a significant amount of privilege.
Now, let's stop and think about all the places where that password might be written down. We probably don't have it in any obvious location, like a a sticky note attached to the back of our monitor, but think of the other places it may be saved: i.) Technical configuration document with login details, ii.) Clear text Powershell or batch script iii.) Connection-string in our web.config tying back to our database. These are all just some places I have seen credentials stored in clear text. I am sure you can think of others.
Password Search
Here is a a quick, practical search that we could use with DataGravity to to answer the simple question: Where is there a password written down that I am not aware of?
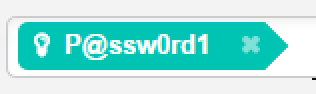
Searching for the double-secret password - in this cae P@ssw0rd1 across the entire IT Department share.
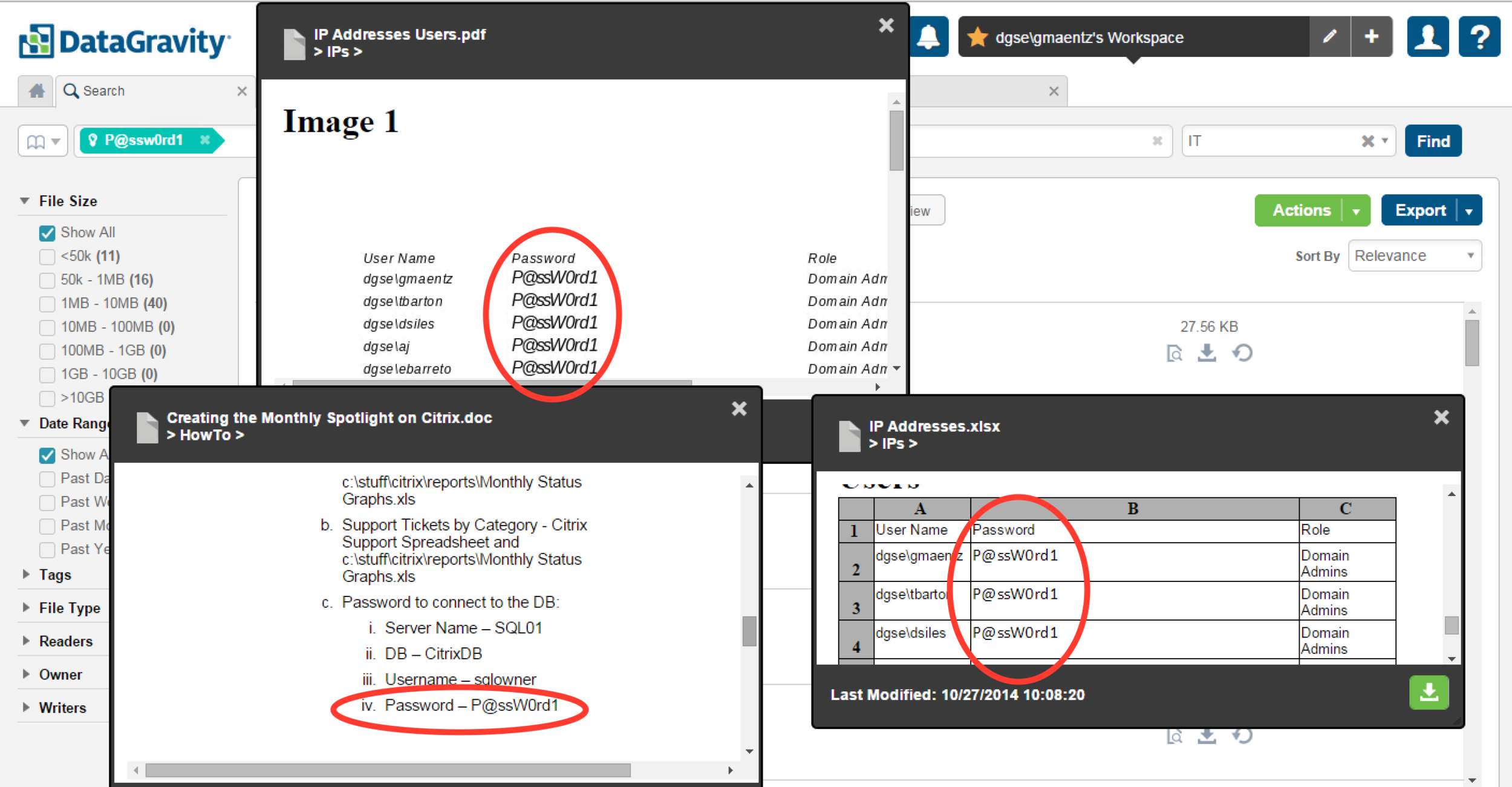
A number of results are returned, so let's take a deeper look at some of the files.
Three different files, all containing our double-secret password - spelled out in clear text.
Let's take a look using the Experience View to see who is reading these files. Should all of these people have access and be reading files that contain clear text passwords? Especially files containing our double-secret password.